Port3 Network: Attacked due to a boundary condition validation vulnerability in the cross-chain token solution CATERC20
ChainCatcher reported that Port3 Network released an incident report on platform X regarding a hacker attack. Port3 Network stated that it adopted NEXA Network's cross-chain token solution, CATERC20. However, CATERC20 has a boundary condition verification vulnerability. After the token ownership is renounced, the function returns a value of 0, which happens to meet the ownership verification condition. As a result, the ownership check fails, making unauthorized access possible. This issue was not pointed out in the CATERC20 audit report. Since Port3 tokens had previously renounced ownership to achieve greater decentralization, they are currently in this vulnerable state.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Data: 21.0483 million STRK transferred to a certain exchange, worth approximately $3.14 million
Wormhole Labs launches Sunrise, a standardized liquidity gateway for external assets entering Solana
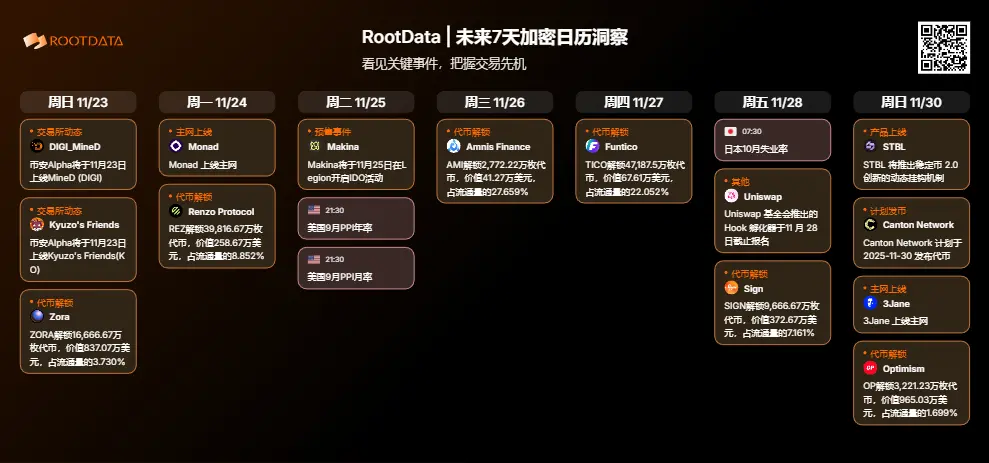
Next Week's Key Events: Monad to Launch Mainnet; Makina to Hold IDO Event on Legion